
Do enough people know how contact tracing works?
One of my favorite weekly news wrap-up shows recently covered an interesting story.
It was from the Telegraph and entitled, “Millions ‘unwittingly tracked’ by phone after vaccination to see if movements changed.“
The article’s contents are interesting – if not unsurprising – to those against the rising Surveillance Oligarchy. But the reversal from “contact tracing” the supposed ill to instead surveilling the vaccinated is worth noting, as is the method of tracing described in the article.
Is humanity aware of the multivariate methods of contact tracing beyond the toggle switch in iOS and Android?
And just how do the methods being used by the Anglo-American Establishment at Oxford University in the above Telegraph story differ from those being dreamt up by Silicon Valley?
The short answer is that multiple entities (namely your cell carrier, Google, Apple, and their State and corporate affiliates) are all vying for their position in the emergent Panopticon. The long answer has to do with resolution and accuracy of metadata, but we’ll get to that momentarily.
Most people know that contact tracing is a form of person-to-person surveillance using cell phones. Some know that Bluetooth is involved. Others are aware that cell carrier data can be used for contact tracing directly.
The deeper story lies in how each of these methods is accomplished, and by whom.
In this article, we’ll take a look at the technicals of contact tracing – examining the (limited) source code and source documents where possible and unveiling other engineering methods utilized where we can.
Apple <3 Google: A Match Made in Hell
The first time Apple and Google crossed paths, Google CEO and Apple board member Eric Schmidt silently stole the concept for Android from Apple’s iOS.
The two operating systems now account for nearly 60% of all web traffic.
So it is no surprise that these surveillance titans, after cornering most of modern web traffic, turned to weaponize it under the auspices of a public health crisis in May of 2020.
Despite a propaganda push to ensure the public that contact tracing surveillance data is “private,” it is anything but – while a lone hacker may have trouble fetching and decrypting packets sent by this contact tracing API, the companies behind contact tracing and their affiliates have already pwned you.
Apple and Google can ruminate all they want that their contact tracing data being sufficiently encrypted and private:
…yet their own API documentation reveals that all contact tracing is done on the Big Tech surveillance grid:
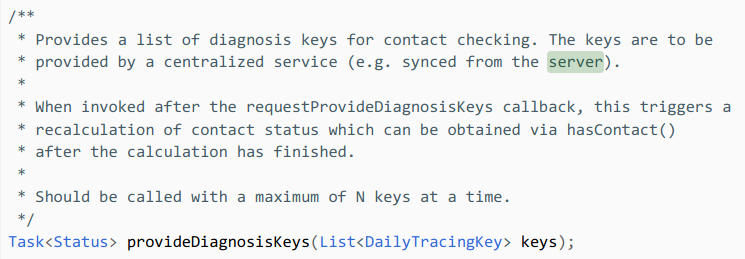
This code from Google’s contact tracing API (or Application Programming Interface), is closed-source and unauditable. But for the layman, the concept of the API is simple – it’s a bit of code that performs calculations from a third-party server and returns data to whoever asked for it.
In the case of Apple and Google’s contact tracing API, they’re the ones crunching the numbers. And they can share those results with whoever they want – governments, health insurance providers, police, intelligence agencies, you name it.
This doesn’t sound very private to me.
Even if identifiers to these API calls are 100% anonymized and encrypted, Apple and Google can still associate your identity based on your Gmail or iCloud device login. In other words, the opposite of private.
While both Apple and Google have alleged methods to disable contact tracing in their settings, there is no way of verifying that this functionality is actually turned off. Apple’s code is entirely closed-source, and while the Android Open Source Project is fairly open, Google’s contact tracing and gApps code is anything but.
-
 Degoogled OnePlus 7T (128GB)$599.99
Degoogled OnePlus 7T (128GB)$599.99 -
 Degoogled Pixel 4a (128GB)$649.99
Degoogled Pixel 4a (128GB)$649.99 -
 Degoogled Moto G7 Play Smartphone (32GB)$299.99
Degoogled Moto G7 Play Smartphone (32GB)$299.99
And like any good future-proof protocol, the contact tracing API is extensible – in other words, its spec allows transfer of data over Bluetooth that can be defined in the future which may or may not have anything to do with alleged “health” screening:

If Big Tech is good at anything, it’s stacking functions; today’s contact tracing API to fight a supposed global health menace is tomorrow’s turnkey vaccine passport (or social credit system). And the associated metadata predefined by the contact tracing Bluetooth spec demonstrates that additional capabilities were planned from the beginning.
Google has been performing hyperaccurate location snooping via WiFi triangulation for nearly a decade. Contact tracing is simply the latest iteration – spying from device-to-device via Bluetooth. This technology has likely existed for many years as well.
What is surprising is its blatant openness.
While both Apple and Google attempt to bedazzle users with talk of public-private key cryptography on intake servers, make no mistake – every phone with iOS or a Google account installed has a unique fingerprint, which makes associating an encrypted key with your identity relative child’s play:

Given that we have no idea what other metadata is logged by these “ingestion servers” or the associated database schemas, this assurance of anonymity is no more legitimate than a condo on Olympus Mons.
Both Google and Apple took this surveillance apparatus to new heights in late 2020, offering to collate data directly for State agencies without the need for them to build their own applications. Surveillance as a Service.
Yet in a world where cell phone carriers and three-letter agencies already have so much data about us, why have Apple and Google gone to such great lengths to establish their contact tracing APIs?
Privatizing former State apparatuses is one reason. Most people “consent” to smartphone Terms and Conditions, which are admissible in court. It’s hard to say that anyone consents to what happens in Bluffdale, Utah.
But another is granularity of data – Apple and Google already have a direct pipeline into your digital existence, no backdoors required. They log your location. Your emails. Your text messages. Any alert popup whatsoever, an oft-overlooked surveillance tool. Your speech. Even the way you move via accelerometer.
Why steal what is given freely?
Pipelining this data directly to the highest (or most powerful) bidder is an obvious information warfare benefit.
And your cell carrier wants in on the action, too.
Oxford University and the Cell Carrier Snoops
The kind of “vaccine tracing” surveillance described by the Telegraph is a completely different beast. Rather than utilize the contact tracing API data, Oxford University opted to go to cell carriers directly:

Oxford couldn’t take advantage of the contact tracing technology above (yet) as they were explicitly tracking those who’d taken the jab, not those diagnosed with the magic virus.
But as a relatively competent programmer myself, I bet they wish the contact tracing API could fulfill this mandate. The resolution of data and amount of potential information collected is simply much more personal, and in turn, accurate, when using Apple and Google’s API.
And as described above, Google and Apple’s Bluetooth specification is already extensible enough to support this use-case in the future.
Given these limitations, Oxford went to cell phone carriers directly. And there’s still a good amount of data to collect at the cell tower level, from the IMEI (device identifier) to the IMSI (carrier customer identifier). So the above assertion that the data collected is not “individual surveillance” is patently ridiculous, as there’s at least two unique identifiers collected by cell towers off the top of my head.
With 5G, this information nexus expands rapidly.
High-gigahertz spectrum RF like 5G is something of a trade-off – it allows significantly greater resolution of location data on urban serfs and far greater speed of data transmission while making only incremental surveillance gains in the countryside.
So if you are tracking a city like, say, London, for “vaccine reactions,” 5G fits the bill pretty well. What’s good for the goose is not necessarily good for the gander, as they say.
Yet this is also a prime example of mutual back-scratching – while telecoms themselves have a role to play in the emergent Surveillance Oligarchy, cell phone OS companies also stand to benefit from emergent 5G technologies. Imagine a future where Google and Apple have the bandwidth at the cell tower level to “livestream” your camera and microphone perpetually without your consent.
No need to imagine, as in many urban environments, this future is the present.
In Closing
In this article, we’ve examined two methods of how contact tracing works – the Silicon Valley API method and the cell carrier method, how both can be weaponized for either “health” screening or vaccine tracing, and how the latter’s methods ultimately enforce the former.
As an individual, what can be done to opt out?
Clearly, ticking off the “no contact tracing” option in your smartphone’s settings is simply not sufficient. Especially in a world where vaccine passports will soon supplant “illness” tracing using the same underlying technology.
If you’re using an iPhone, the solution is simple: Pitch it.
If you’re using an Android smartphone, you at least stand a chance against API metadata aggregation, the most dangerous form of corporatocratic surveillance described in this article.
Your ultimate solution is to degoogle – the Android OS is, for the time being, open-source. This means you can flash your own variant of Android without Google, or if you’re so inclined, purchase a degoogled phone directly.
There’s not much that can be done regarding carrier tracking aside from pulling your SIM card or ditching your phone entirely – even flip phones are no longer a viable alternative, with the phaseout of 3G and Google’s recent purchase of KaiOS.
The emergent digital Panopticon is rapidly taking shape around us, and while the front door slammed shut in May of 2020, there are still windows of escape.
Seize them while you can.
[…] we have covered in previous posts, there is no simple way to disable contact tracing on your […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] wir in früheren Artikeln beschrieben haben, werden derzeit weite Teile des staatlich kontrollierten Panoptikums an […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
[…] nous l’avons décrit dans des articles précédents, de vastes pans du Panopticon contrôlé par l’État sont actuellement sous-traités à des […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]
So is there contact tracing on a flip phone?
At present, there’s no contact tracing on flip phones. However, given Google’s recent Series A investment in KaiOS, the largest feature phone OS provider, it’s likely that flip phones will include some form of contact tracing in the future.
Unfortunately, the days of the flip/feature phone are rapidly coming to an end, with most US carriers pledging to phase out 3G by the end of 2022. As ARM-based processors get increasingly powerful and efficient, even the humble flip phone will soon be capable of the same surveillance tech as smartphones, but with even less choice in terms of operating system.
[…] https://www.bibliotecapleyades.net/sociopolitica/sociopol_internetgoogle.htmhttps://www.washingtonpost.com/wp-dyn/content/article/2010/02/03/AR2010020304057.htmlhttps://www.theguardian.com/news/2018/dec/20/googles-earth-how-the-tech-giant-is-helping-the-state-spy-on-ushttps://www.corbettreport.com/just-be-evil-the-history-google-doesnt-want-you-to-know/https://www.forbes.com/sites/thomasbrewster/2021/03/10/fbi-uses-google-location-data-to-ensnare-alleged-capitol-hill-rioter/?sh=145265ff104ehttps://privacytogo.co/shop/https://www.bibliotecapleyades.net/sociopolitica2/sociopol_greatreset.htmhttps://en.wikipedia.org/wiki/Jigsaw_(company)https://www.bibliotecapleyades.net/esp_sociopol_cfr.htmhttps://www.bibliotecapleyades.net/sociopolitica2/sociopol_greatreset.htmhttps://en.wikipedia.org/wiki/Jared_Cohenhttps://www.bibliotecapleyades.net/sociopolitica/sociopol_clinton.htmhttps://web.archive.org/web/20180315211120/http://washingtonsblog.com/2016/09/three-big-lies-pervade-americas-news-media.htmlhttps://web.archive.org/web/20120329130644/http://english.al-akhbar.com/content/stratforleaks-google-ideas-director-involved-%E2%80%98regime-change%E2%80%99https://pando.com/2016/03/21/new-clinton-emails-show-how-google-collaborated-us-state-department-try-oust-assad/https://www.bibliotecapleyades.net/sociopolitica/sociopol_syria.htmhttps://jigsaw.google.com/https://jigsaw.google.com/https://www.bibliotecapleyades.net/imagenes_sociopol3/internetgoogle94_02.jpghttps://www.youtube.com/watch?v=PPdQCw0oRA0https://en.wikipedia.org/wiki/Jigsaw_(company)#Redirect_Methodhttps://privacytogo.co/shop/https://jigsaw.google.com/https://www.bibliotecapleyades.net/imagenes_sociopol3/internetgoogle94_03.jpghttps://en.wikipedia.org/wiki/Jigsaw_(company)https://privacytogo.co/how-contact-tracing-works/https://www.technocracy.news/five-eyes-biden-authorizes-access-to-everyones-social-media/https://www.lewrockwell.com/2021/06/james-bovard/bidens-buffoonish-war-on-extremism/https://www.sysjolt.com/2021/every-modern-computer-has-a-backdoor/https://www.goodreads.com/book/show/34220713-surveillance-valleyhttps://www.corbettreport.com/data-is-the-new-oil/https://privacytogo.co/lineageos-vs-grapheneos/https://whatthezuck.net/wtz/ […]
[…] we’ve described in previous articles, vast swaths of the State-controlled Panopticon are currently being outsourced to Big Tech […]