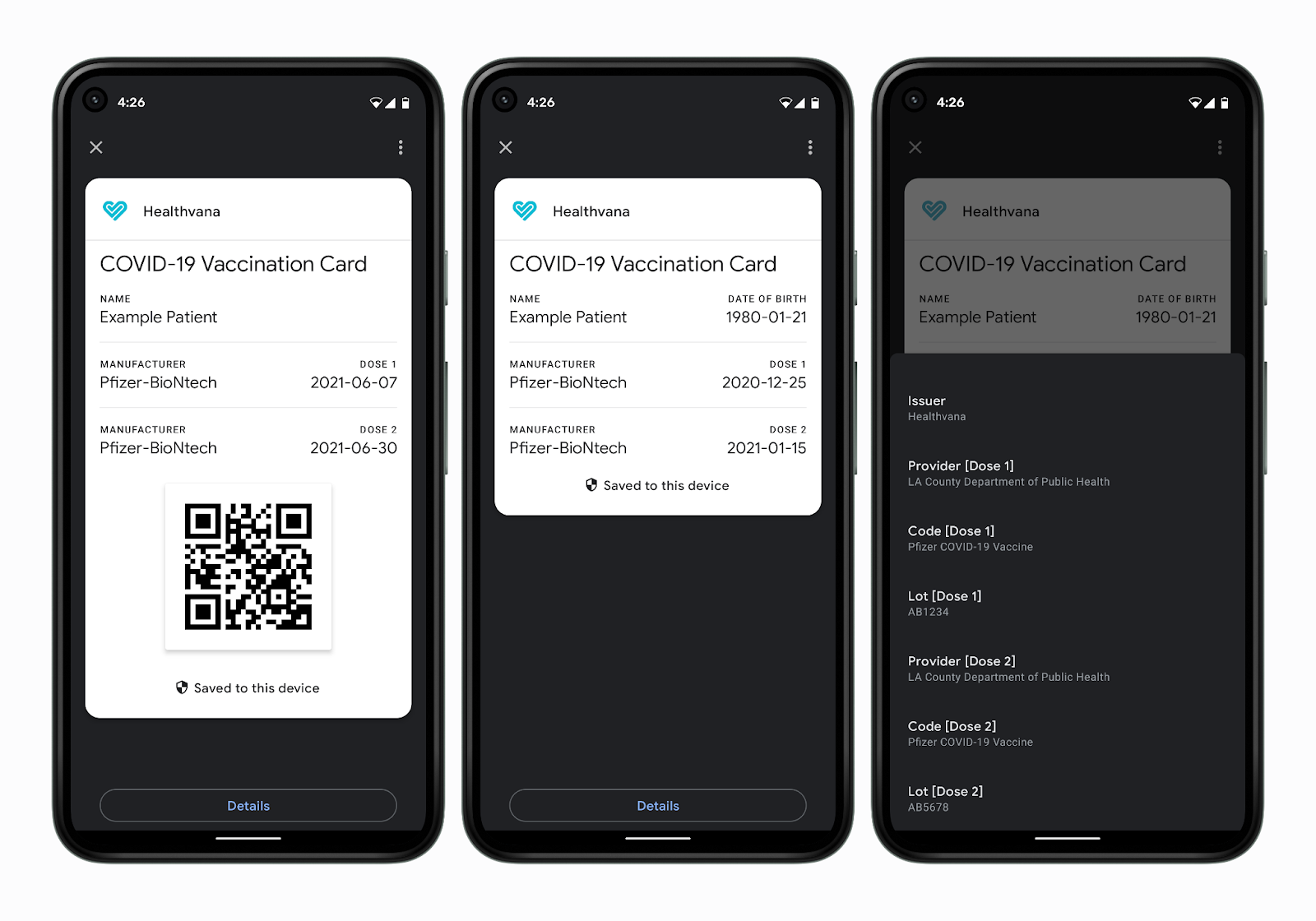
On June 30th, 2021, the Google Developers blog announced the launch of vaccine passports in Android through its Passes API.
Less than 24 hours later, the European Union, long mired in a sea of national standards for digital jab records, rolled out its EU-wide vaccine passport.
Two completely different vaccine passport schemes unveiled on the same day, encompassing the whole of the Western world? What are the odds!
Exceedingly low, of course. This level of coordination belies yet another blitz in the ongoing rollout of a global, technofeudal control grid. The EU has arguably been at the forefront of this rollout – its standardized digital jab certificate is little more than an aggregator for the draconian technology now operating at the Nation-State level.
Adoption of this unified standard is already approaching 100% of EU Member States. Doublethink rhetoric of restoring the Schengen Area’s “freedom of movement” abounds, even as additional barriers to travel are erected.
In this sense, Google and the US are playing catch-up. While de facto vaccine passports have been implemented sparingly in places like New York, California, and Hawaii, an ever-expanding number of States have banned the notion outright.
Yet herein lies the insidiousness of the public-private partnership model: Technocrats can use governments where it suits them, corporations where it does not, and an increasingly bizarre fusion of the two where necessary. Even the propaganda rollout surrounding jab passports is bifurcated by this model, with the EU using official government bulletins while Google syndicates the news via trendy tech blogs.
And though many States in the US have passed legislation or executive action to curb the implementation of vaccine passports, Google could care less.
Google Passes: Vaccine passports for all, regulation be damned
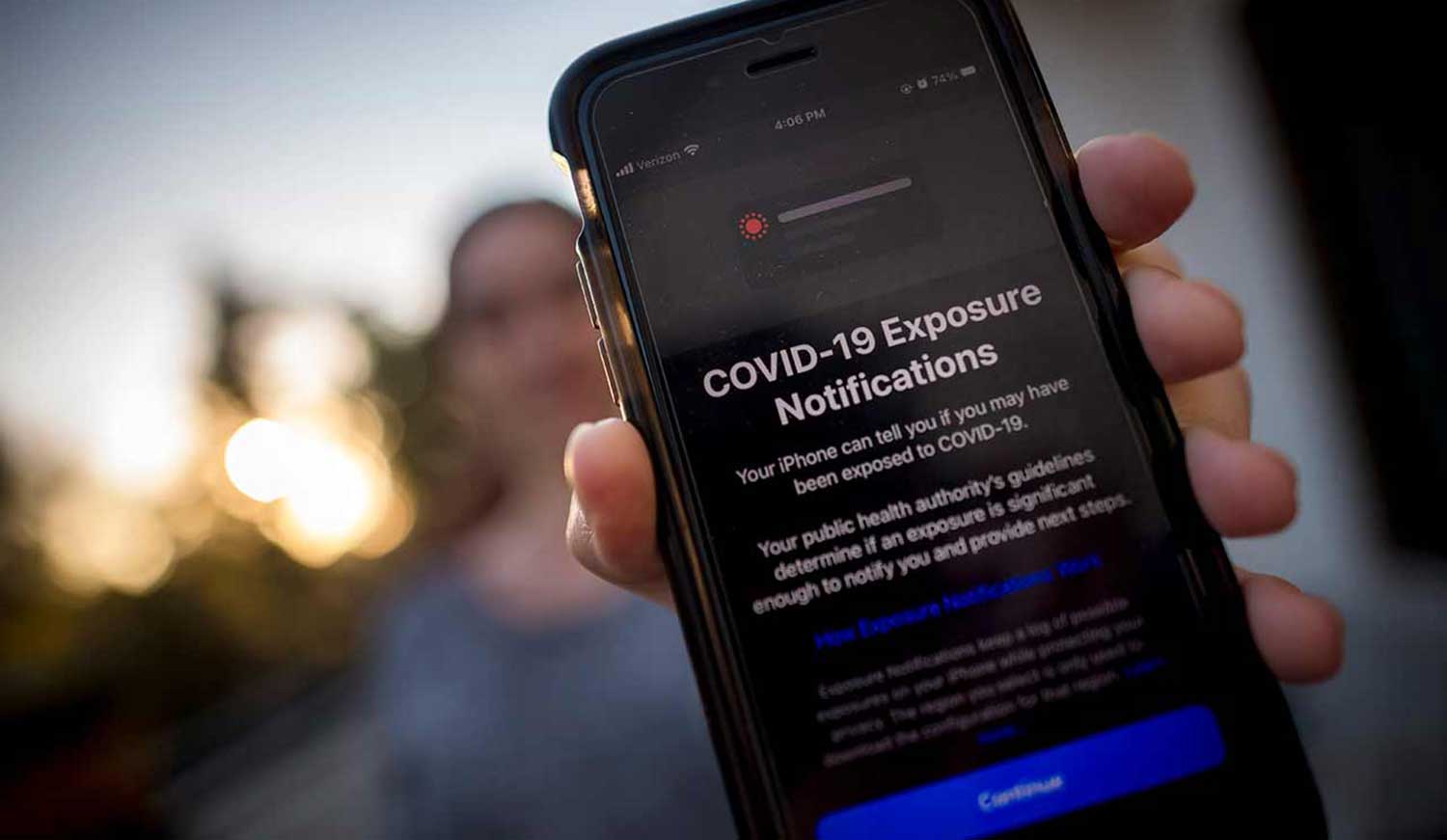
Like the contact tracing API before it, political resistance alone is proving ineffective against the technological implements of the Great Reset. Even the staunchest State level opponents to this agenda have done nothing to halt the hyperactive Bluetooth surveillance grid running on Android and iOS devices – on the contrary, many have used taxpayer money to help finance its data harvesting operations.
Similar political action against digital vaccine passports will not halt Google’s rollout via the Passes API, either.
In fact, Google’s selection of the Passes API to implement vaccine records is telling in its own right, given the information it already stores: Boarding passes for airlines. Travel tickets. Event tickets.
While legislative action in States like Florida may allow you to attend a Miami Dolphins game with your biological privacy in tact, the same may not be said for travel. The battle over Federalization of airline travel was lost on November 19th, 2001 with the creation of the Transportation Security Administration, whose influence has been expanding ever since – the latest privacy affront being the REAL ID Act, which mandates highly insecure RFID technology for interstate air travel.
-
 Degoogled Moto G7 Plus (64GB)$374.99
Degoogled Moto G7 Plus (64GB)$374.99 -
 Degoogled OnePlus 6T (128GB)$449.99
Degoogled OnePlus 6T (128GB)$449.99 -
 Degoogled Moto G7 Play Smartphone (32GB)$299.99
Degoogled Moto G7 Play Smartphone (32GB)$299.99
Even more dangerous are biometric companies with government contracts, like CLEAR, whose terminals are already widely used at TSA PreCheck terminals and event centers.
Google Passes and other digitized jab certificates are simply a competing product. One that is already in the pocket of 85% of Americans alone, with similar adoption levels in Europe.
Products marketed for “convenience” like TSA PreCheck biometrics will, over time, become mandatory – the REAL ID Act itself is a perfect example of this Fabian creep. Passed all the way back in 2005, its full implementation has been pushed back multiple times due to individual State holdouts, most recently until 2023.
But these delays are immaterial – the framework’s existence is all that matters, as despite not being enforced, privacy-violating RFID technologies are now the norm for US driver’s licenses. Jab certificates like Google Passes will be no different. Once in place, they will be utilized – if not immediately, then in the future.
Not only can the Passes API integrate with third-party pharmaceutical companies to track jab history, it is also capable of storing results from dubious PCR tests. This level of biodigital convergence sets an unsettling precedent, as Silicon Valley’s expectation is that your medical history will now be in your pocket at all times, integrated with their servers, and subject to whatever authority may ask for it.
Passes is not an isolated product, either – it’s a development suite within the broader Google Pay SDK.
There are technical reasons why Google may have chosen to use the Pay SDK as opposed to a health-focused API like Google Fit – QR code generation, limited use passes, and encrypted keyrings are already present in the Passes API. However, despite Google Pay’s scant consumer use at present, the long-term intent is crystal clear: Access to financial services and medical records will be intertwined.
In Closing
The post-2020 era has pushed humanity to the precipice of a longstanding dream of our would-be comptrollers. Whether it is Newt Gingrich’s Age of Transitions or the late Zbignew Brzezinski’s Between Two Ages, the kind of biodigital convergence represented by digitized medical passports has been at the forefront of the Technocratic agenda for decades.
As Silicon Valley attempts to bridge the “last mile” of mandated biometric surveillance, resistance to these aims on an individual level remain multivariate – ditch your smartphone, or at least utilize a privacy-respecting alternative that is incompatible with Google or iOS services. Starve the business of travel and entertainment industries that would see us become serfs in exchange for bread and circuses.
If you’re in the EU, use paper records instead of digital equivalents, or better yet, refuse to comply at all.
Educate well-meaning policymakers to the threats represented by the pseudo-private sector and impress upon them that the dangers of State surveillance are rapidly being outpaced by Terms and Conditions mandated by smartphone companies.
Neofeudal Technocracy is desperately trying to extract humanity’s consent to these draconian efforts before the next phase of the so-called Great Reset.
Don’t let them.